NIST or CIS Cyber Security Frameworks... Does it Matter to ITAM?
The Perpetual Process Behind an Accurate Inventory
Regardless of which cyber security framework your organization has chosen (or will choose), an accurate IT asset inventory is a requirement. It's important to note that maintaining an accurate IT asset inventory is an ongoing process rather than a one-time event. Let’s start by briefly examining what IT asset lifecycle management entails.
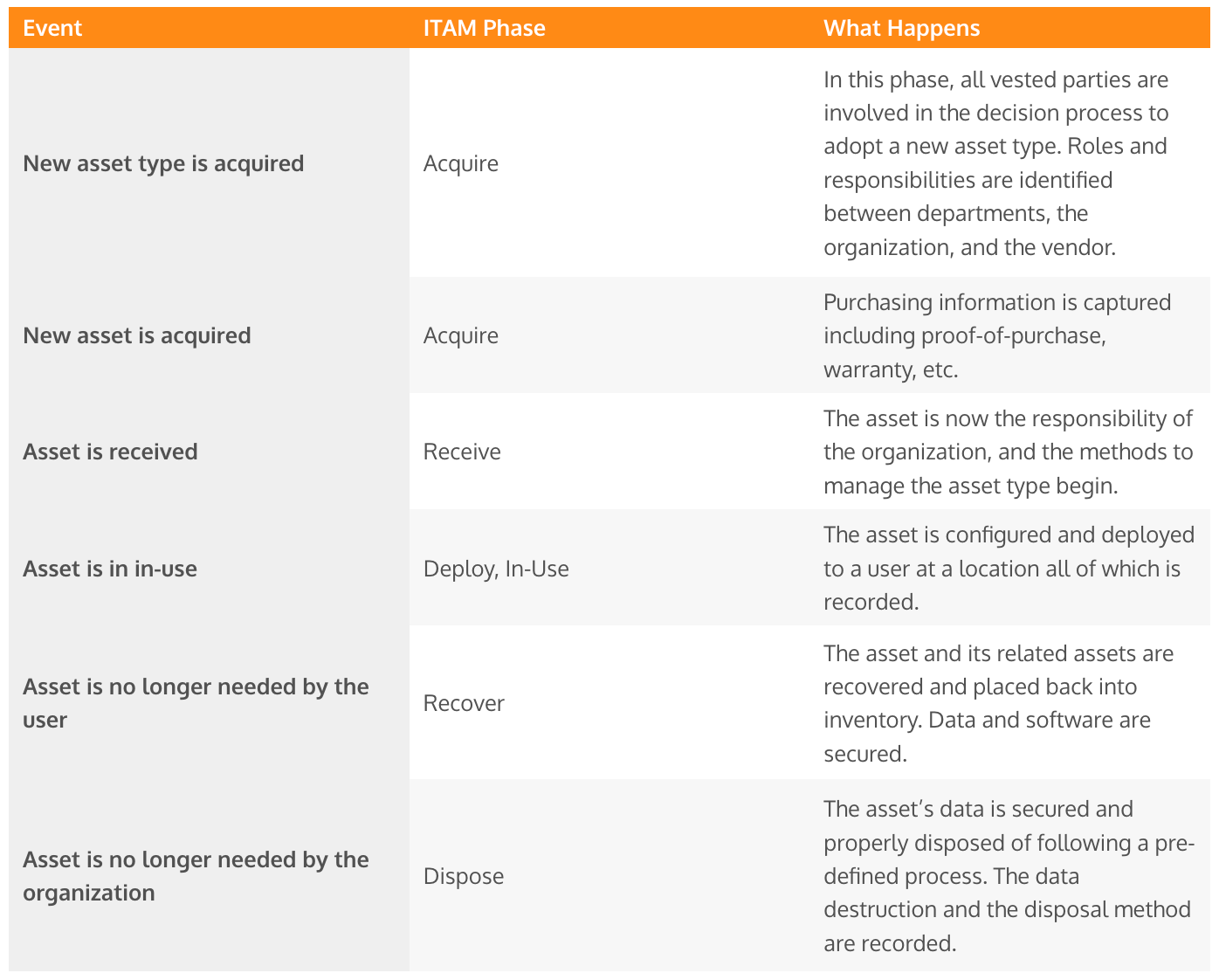
| Event | ITAM Phase | What Happens |
|---|---|---|
| New asset type is acquired | Acquire | In this phase, all vested parties are involved in the decision process to adopt a new asset type. Roles and responsibilities are identified between departments, the organization, and the vendor. |
| New asset is acquired | Acquire | Purchasing information is captured including proof-of-purchase, warranty, etc. |
| Asset is received | Receive | The asset is now the responsibility of the organization, and the methods to manage the asset type begin. |
| Asset is in in-use | Deploy, In-Use | The asset is configured and deployed to a user at a location all of which is recorded. |
| Asset is no longer needed by the user | Recover | The asset and its related assets are recovered and placed back into inventory. Data and software are secured. |
| Asset is no longer needed by the organization | Dispose | The asset’s data is secured and properly disposed of following a pre-defined process. The data destruction and the disposal method are recorded. |
Although the above description may seem simple, much more is happening behind the scenes. For instance, the IT Asset Management (ITAM) program identifies and oversees the electronic waste disposal vendor. And a lot of data is being generated by different departments. This data must be curated to create meaningful information and linked to the asset. From one perspective, the ITAM Program operates in the same way, regardless of the security framework in place. However, the specific details of the framework may require the ITAM Program to make some adjustments.
Cyber Security Frameworks and The ITAM Program
Two of the most well-known and widely adopted IT security frameworks are from NIST (National Institute of Standards and Technology) and CIS (Center for Internet Security). NIST’s framework includes 23 Functions and 108 Categories, which can be matched with ITAM Program elements in over 300 ways. Similarly, CIS’ framework has 19 Controls and 161 Safeguards that can be mapped to ITAM Program elements in over 400 ways.
Organizations choose between NIST or CIS based on their needs. The NIST framework is more abstract and has been adopted by larger organizations. Meanwhile, CIS provides greater detail and is often adopted by smaller organizations.
Many IT frameworks and IT Asset Management (ITAM) share a common trait in how they mature - starting small and gradually improving over time. There is a symbiotic relationship between these two areas, with a more mature ITAM program accelerating the maturity of frameworks. However, a key difference between the two is that IT security is a vertical function with horizontal requirements, whereas ITAM is a horizontal function with horizontal requirements. When implemented correctly, ITAM can benefit not only IT security but also other stakeholders such as finance, IT, HR, legal, etc. This means that ROI on ITAM improvements is often higher than those made within verticals.
Many organizations still struggle with IT security. The threat from malicious actors is constantly changing and seems to be never-ending. While it may not directly add value to the organization, security is crucial and cannot be ignored. We must accept this reality and focus on making the most of our IT security investment while safeguarding our data. What steps can we take moving forward?
Securing the Data
The role of the IT asset manager includes acquiring knowledge about IT security and enhancing the ITAM Program to facilitate IT security endeavors. Both roadmaps should complement each other for a cohesive approach toward achieving the common objective.
IT security professionals must work closely with ITAM and fully comprehend how it can effectively reduce their workload. ITAM is essentially the proactive arm of IT security and should be utilized accordingly.
IT professionals should collaborate with ITAM and IT security as many IT processes generate data that these departments require. The key challenge is ensuring that the data produced is high quality and deemed trustworthy.
IT security requires participation from everyone in the organization. What better discipline to support IT security in this endeavor than ITAM, which also requires everyone’s participation? The return on an organization’s investment in IT security is multiplied when ITAM is included. This increase in ROI is not only measured in euros, pounds, or dollars it is also, and perhaps most importantly, measured in the protection provided to your organization’s data.
More on Cyber Security
What's Next?
Our ITAM/NIST/CIS mapping and training blaze the trail to protect what's most important, the data. Click here to learn more about the ITAM / Cyber Security Workshop
ITAM IQ Is Your Gateway to Modern ITAM
Our expertise enables individuals to advance their ITAM program for the future by providing next level IT Asset Management best practices knowledge. These practices create a symbiotic relationship between ITAM and departments such as IT Security, IT, Finance, and HR by working in tandem to provide heightened information quality which significantly reduces risks, creates greater financial benefits, further enhances compliance, and increases efficiencies.
Where to next?
-
General IT Asset Management
Learn more →We have the practical, best practice knowledge you need.
-
Cloud Asset Management
Learn more →Whether you are contemplating digital transformation or are currently managing SaaS, PaaS, and IaaS, we are here to guide your way.
ITAM and Cyber Security
We will show you how ITAM can be IT Security's proactive arm.
ITAM IQ Newsletter
Copyright ©2021-23 ITAM IQ | Akron, Ohio USA | All Rights Reserved