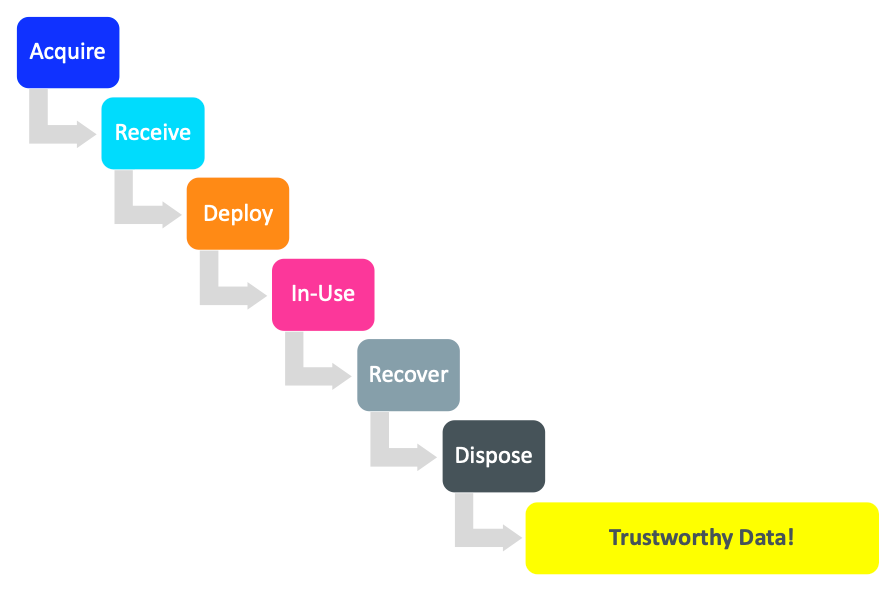
ACQUIRE
ITAM starts when someone thinks they need an IT asset. Ideally, ITAM is asked to match the user’s requirements with what is currently part of the IT portfolio.
The
request process will take one of two paths depending on whether the request is for an asset that is part of the IT standards. If the request is for a standard asset, the Visio application for example, then the
approval is based on the user’s entitlement which is driven by the user’s assigned role.
Suppose the
request is for a non-standard IT asset. In that case, the request is evaluated for business value and assessed to determine its impact on the organization. It includes all parties with a vested interest, as described in the prior section, The IT Asset Ecosystem. Based on the recommendation of those parties, the appropriate individual denies or approves the
request, and the asset is
procured.
RECEIVE
All IT assets follow a well-defined
receiving process that records the receipt after the asset passes the
acceptance criteria. The
receiving process applies to all assets, not just those owned by the organization, including vendor-provided assets and BYOD employee-owned assets. All assets entering the organization’s network must be recorded. IT assets not ready to be deployed immediately are stored securely. All information associated with an IT asset is
stored in the ITAM repository.
DEPLOY
The deployment process is critical because the asset must be
configured appropriately for the end-user, IT, and IT Security. The
installation process records the asset’s location, end-user assignment, department, and cost center.
IN-USE
Bad things can happen to IT assets after they are deployed. The asset can be moved, lost, or stolen. The asset’s configuration can change. A perfect example is software. Software is constantly being updated, changing the system’s configuration. These updates can break functionality or introduce new security issues. The
move,
add, and
change processes must accurately record changes made in the ITAM repository.
RECOVER
The purpose of the Recover phase is to
recover IT assets that are no longer in use. There are several benefits to recovering assets that are no longer needed including:
- The asset can be placed in inventory, making the asset available for redeployment. This increases the ROI of the asset.
- The asset is secured and is not at risk of being lost, stolen, or misused.
- Data stored on the asset is backed up if required and secured.
- IT assets related to the asset being recovered are also recovered. For example, the recovery of a smartphone will also include the recovery of its related assets – the cellular plan and any allocated server licenses.
- Finally, the recovered and related IT assets are securely
stored in inventory for future redeployment. The assets’ status is updated in the ITAM repository.
DISPOSE
The final phase of an IT asset is the Dispose phase, and it is just as critical, if not more critical, than the previous phases. The phase is similar to the Recover phase, with identical
Secure Data and
Recover Related Assets processes. The
Finance process “closes the books” on the asset, including final calculations for ROI and TCO. The asset is formally retired, meaning hardware assets are appropriately processed, and all other asset types (software, cloud, etc.) follow the disposal process defined for that asset type. A request is made to finance to determine if the asset is being depreciated. If the asset is being depreciated, then the asset is placed in secured storage for the appropriate term. All other parties, including users, IT, IT Security, and vendor management are notified the asset has been disposed.
The Disposal phase also supports the “disposal” of vendor and employee-owned IT assets. Of course, these assets are not being disposed of traditionally, but they are leaving the organization, so data must be secured and related assets recovered.